Preventing Email Malware Attacks
The public idea of hackers and cyber-attacks has been mostly informed by their portrayal in pop culture: the image of a mysterious hooded man, concealed in shadow, typing in the coding equivalent of technobabble. Because of that icon of the hacker, it would surprise many people that, in the real world, their most useful tool is something so commonplace: email.
Even though more elaborate methods of delivering targeted cyberattacks are growing, email still shows to be the most common channel for these attacks. According to a 2021 global survey of 1,100 IT professionals, ransomware attacks hit 80% of those surveyed organizations in the past year. Alarming still is that 92% of malware is delivered through email. It simply takes one member of the organization to provide the perfect circumstances for a data breach and cost the company consumer trust and revenue.
Common types of email cyberthreats
- Spam
Spam is not targeted, nor is it elaborate. This method is the continuous, unsolicited sending of email messages, containing malware, to a large pool of people. The idea behind this strategy is that sending out emails to so many individuals statistically means that a fair amount of malware attacks will be successful. It’s casting out such a large net that there will be a couple of good returns for hackers.
- Phishing
Phishing entices and tricks a person into divulging personal info, such as bank account info, social security numbers, or sensitive company data. Instead of casting a wide net like spam, phishing is more targeted. Phishing emails are designed to look like they come from legit organizations to garner trust. Some could contain links that take the individual to a malicious, phony page to enter in their information.
Another form of phishing can occur when a business email account from within the company is compromised and a hacker uses it to phish information out of other coworkers. S
poofing is also common in which the hacker creates a look-alike fake account of a legit person/company. If a person were to receive an email from a spoof account, it could appear to be from a boss or their bank asking for their personal info.
In 2020, phishing emails were a leading point of entry for ransomware, amounting to about 54% of digital vulnerabilities. It is important to note that poor user practices and lack of cybersecurity training were also significant contributors to those vulnerabilities.
Tips to mitigate threats by email
- Use email authentication
This practice reduces the likelihood that an email is compromised. It also helps to verify that the email truly comes from who it claims to be from. Usually, this is implemented by your company’s servers which analyze the email to verify it comes from a legitimate domain.
- Train employees on how to detect malicious emails
Share with them some ways of identifying suspicious emails, such as the email address not matching who the email says it’s from. Also, refresh them on small security steps. Some of these steps are not visiting unsecured websites and not clicking on links in emails without verifying where the link will take them.
- Keep your security up to date

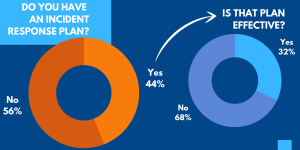
Despite the rise in threats mounting, especially with the rise of remote work, 56% of organizations lack an incident response plan. And only 32% of the remaining 44% believe that their plans are effective. Even if a threat originates from something as small as an email, it can quickly become a company-wide threat level. Therefore, it is important to examine current company security plans and makes sure it offers comprehensive protection to match up to today’s threats.
With FirstComm’s recent launch of our Secure XDR platform, we are now equipped to provide our customers with fully automated breach protection
FirstComm Secure XDR (powered by Cynet) is purpose-built to deliver complete protection, monitored by the 24/7 MDR team. Secure XDR platform includes NGAV (Next Generation Anti-Virus) EDR (Endpoint Detection and Response) NTA (Network Traffic Analytics) UBA (User Behavior Analytics) Deception & CLM (Centralized Log Management).
Click here to read more info: https://bit.ly/3lbHgOh